Web applications have become an inherent part of our day-to-day life. From shopping online to scrolling through social media, there is nothing that we don’t use web applications for. But the more people use the public internet for their work, social networking, and shopping needs, the more likely malicious cybercriminals are to keep honing their skills for stealing information. This makes web applications the soft underbelly of organizations. Where once a teenager with no criminal record and a knowledge of archaic English would have been a typical hacker, today’s attackers are much more likely to be sophisticated and well-funded people who work for organized crime rings or nation-states.
Now, we are going to explore what are the 10 most common web security vulnerabilities in 2023 and practical interests to help you avoid them.
Let’s dive in!
Top 10 Web Application Vulnerabilities
1. Injection Attacks
What it is?
Malicious injection, also known as SQL Injection and Cross-Site Scripting (XSS), is one of the most common and likewise one of the gravest web application vulnerabilities. It is about an attacker inserting harmful instructions into a website’s database so that it modifies the program of the website, corrupting the data and resulting in unauthorized access to the user’s data.
Prevention
- Use parameterized queries to prevent SQL injection.
- Employ input validation to filter out malicious input.
- Implement output encoding to protect against XSS attacks.
2. Cross-Site Scripting (XSS)
What it is?
XSS is like web application vulnerabilities that can infect your website. It allows you to sneak nasty code into your web pages. Then, when other people view these pages, they might also get infected.
Prevention
- Check and clean user input to prevent XSS attacks.
- Implement a Content Security Policy (CSP) for added protection.
- Control resource loading to reduce XSS risks.
3. Security Misconfiguration
What it is?
Security headers such as HTTP headers or HTML meta tags are important for web application security, and misconfigured or absent headers can create vulnerabilities leading to data leakage and more.
Prevention
- Keep software up to date and patched regularly.
- Limit permissions and access by using the principle of least privilege.
- Use security scanners and other automatic vulnerability discovery tools to identify security misconfigurations.
4. Sensitive Data Exposure
What it is?
Sensitive data exposure is when secret information, like credit card numbers or personal details, accidentally gets into the wrong hands.
Prevention
- Encrypt stored and transmitted sensitive data for robust security.
- Minimize public display of unnecessary sensitive information on websites.
- Treat sensitive data like precious treasure for protection.
Read more – Software Development Process
5. Broken Access Control
What it is?
Broken access control vulnerabilities can allow attackers to access data or perform actions reserved for privileged users. These can have significant consequences for your web application’s security.
Prevention
- Implement proper role-based access control.
- Enforce access controls on the server side.
- Regularly test access control mechanisms for vulnerabilities.
6. Broken Authentication
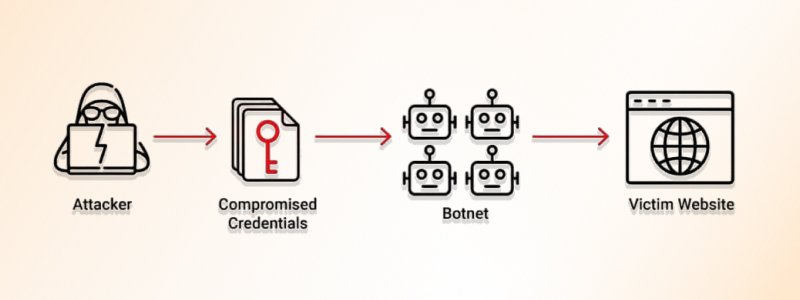
What it is?
Weak or broken authentication mechanisms can leave vulnerable web applications. Attackers may exploit these vulnerabilities to gain unauthorized access, impersonate users, and perform malicious actions.
Prevention
- Implement strong password policies and multi-factor authentication.
- Set session timeouts to limit exposure.
- Regularly audit and monitor authentication logs.
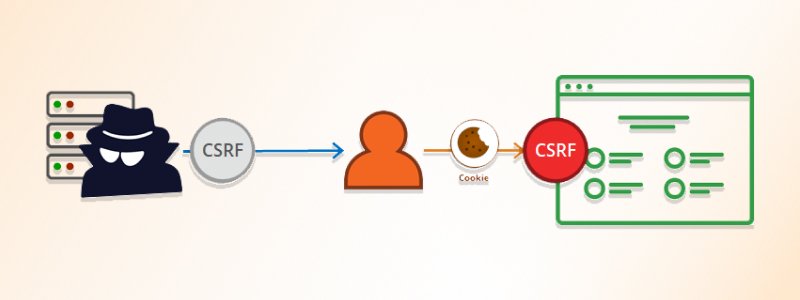
7. Cross-Site Request Forgery (CSRF)
What it is?
Cross-Site Request Forgery (CSRF) attacks induce users to perform actions they did not intend to do. The resulting malicious actions include changing of email addresses of users, changing passwords, and unwanted financial transactions.
Prevention
- Use anti-CSRF tokens to defend your application against CSRF attacks.
- Require users to re-authenticate for state-changing requests.
- Use the Same-Site cookie attribute to make CSRF attacks improbable.
8. Insecure Deserialization
What is it?
Insecure deserialization vulnerabilities occur when an attacker is able to modify the serialized data, potentially resulting in the execution of unintended remote code. This can expose your web application to serious security risks.
Prevention
- Do not deserialize untrusted data.
- Utilize secure deserialization libraries/tools.
- Record and monitor deserialization events for malicious activity.
9. Using Components with Known Vulnerabilities
What is it?
Web applications often utilize various components and libraries. However, using components with known vulnerabilities can make your application susceptible to being exploited.
Prevention
- Keep all the third-party components you use, as well as the components themselves, up to date and if there are any that have known vulnerabilities, unsubscribe from them.
- Keep informed about which vulnerabilities can exist, subscribing to active vulnerability databases and alerts.
- If a component has security flaws that are too serious to serve any useful functionality, delete it or, where possible, find a secure alternative.
10. Insufficient Logging & Monitoring
What is it?
Insufficient logging and monitoring, coupled with missing or ineffective integration with incident response, allows attackers to further attack systems, maintain a persistent presence, pivot to more systems, and tamper, extract, or destroy data. Most breach studies demonstrate the time to detect a breach is over 200 days, typically detected by external parties rather than internal processes or monitoring.
Prevention
- Ensure complete logs are generated. One option is to centralize your logs on servers that are protected against tampering.
- Set up a log server or use a third-party log-management provider to easily collect logs from your web servers, and aggregate, parse, and index them for searching, reporting, and alerting purposes.
- Understand what needs to be logged and what must not be logged—and do so consistently across all applications.
- Alert on indicators of attack/compromise within logs.
- Regularly monitor logs for signs of unauthorized access or activity.
- The effectiveness of any logging mechanism hinges on the user ID and, if applicable, the IP address.
Wrapping It Up
Web application vulnerabilities are a real and persistent threat in 2023 and will be there in the upcoming year. To protect your web application or software development system and the sensitive data it holds, you must be aware of these common security issues and take proactive measures to prevent them. By following best practices and staying informed about the latest security threats, you can ensure the safety and integrity of your web applications.